a new generation of phone authentication
Reliable and rapid authentication continues to be a challenge for businesses and individuals over the phone or with online services. We speak to Simon Jones, consultant with Orange Business, and Richard H Harris, Director at Mobix, about the problems of authentication over the phone and some of the initiatives Orange is working on to overcome them.
why is authentication a big issue?
One of the biggest problems for providers of online and telephone services is authentication. We may live in an age of digital transparency, but it is still very difficult for one party to be sure of another's identity online and on the phone. Being sure that you're dealing with a legitimate party is a tough challenge. All the more tough, when you consider the balance between increased security and usability at a manageable cost.

Traditional authentication techniques for online and telephone sessions between two parties are problematic. Typically, organizations ask questions and expect pre-defined answers from the calling party, such as their mother's maiden name, name of their first pet, or first school. These answers are static, and are easily available online in some cases, in others they can be guessed, phised or vished. When Sarah Palin's web mail account was famously hacked, for example, it was compromised by a college student who researched the answers to her security questions online.
are there any other problems with traditional authentication methods?
The other problem with the traditional challenge-response method is that it only authenticates one party, and that only badly. The other party's identity is never authenticated. So, if someone calls pretending to be from your bank, and asks you questions to authenticate you, you can't be entirely sure that they are legitimate. This gives rise to 'vishing' - the use of telephones for phishing attacks, in which users' sensitive identity information is harvested by imposters.
how can you overcome these issues and be sure you know to whom you are dealing with on the phone or online?
A better solution is out-of-band authentication. This is where both parties are authenticated before the call even takes place. We are doing this ourselves with our partner Mobix and their product Authenticall. When a user registers with the service using the technology, they are given a personal identification number and a user name. They also record a passphrase on the telephone using their own voice.
When the user subsequently logs into the service, it asks them to apply their PIN for authentication purposes. However, it uses a system called PINSafe to do so in a way that doesn't require them to type their PIN.
The user then receives a message offering them the chance to take a call. A code is presented with the message (which can be delivered via a computer or a mobile phone). When the user accepts the call request, the telephone rings, and when the user picks up, the code is automatically read to them. They also hear the passphrase that they recorded when they registered. These two things provide proof that the caller is legitimate, and not an imposter 'spoofing' the call.
what is PINSafe?
PINSafe is already used by many Blue Chip companies globally to secure websites, VPNs and remote access to support millions of users. It sends a ten-digit string to the user who extracts a one-time code from the string using their PIN. In the example below, the user's PIN is 2468, so the second, fourth, sixth and eighth digits are extracted to form the one-time code.
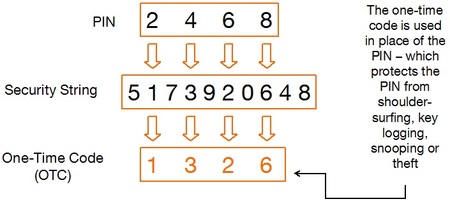
This means that the PIN is never directly typed into the computer, or divulged to anyone on the phone, eliminating the risk of compromise by malicious key loggers or corrupt call centre staff.
how much more secure is the out-of-band authentication approach?
Obviously both parties can be more sure of each others' identity, but it also reduces the time taken to authenticate a user during an actual call. This increases call center efficiency, because in-call authentication is not only ineffective, but also time consuming. On average, organizations take up to two minutes to authenticate an individual in a call, which reduces customer satisfaction levels. Getting authenticated quickly before a call even beings lets customers complete calls more quickly. And because they can authenticate the other party in addition to being authenticated themselves, they feel safer.
As customers can choose when and where to take calls there is also an improvement in customer experience strengthening customer relations, satisfaction and retention.
what's the impact to call center efficiency?
A one second change in the average handling time per call across a 20,000-person call centre operation equates to around £1m per annum. If identification and authentication are handled in band (i.e. on the call) and take between 20 and 120 seconds per call to accomplish it is quite evident to a large organization the savings are colossal (£20m - £120m per annum); even pro rata with a 5000 agent operation the savings are highly significant.
In addition to cost saving, agents become more efficient and can spend their call time in business conversations with customers, make and complete, which in turn increase the yield per agent. Depending on the nature of the call this can deliver increased revenue or better cash flow on top of the cost saving benefits above.
how widely do you expect this technology to be used?
The applications for this technology are broad. Any telephone transaction that must be authorized can be governed by this technology. Telephone banking is one example. Payment authorizations can be made safer and even identifying yourself to a phone or other utility company can be more effectively completed with this technology. We can implement this technology as a managed service for our customers and can integrate it seamlessly with their existing line of business systems.
In the battle against identity theft, vishing, and social engineering, a technology that makes users feel safe at the end of a telephone line is invaluable. It has a positive effect on transactions by making them shorter and on average more successful, while also bolstering confidence in the participating organizations' brand.

After a Masters in Computer Science, I decided that I preferred writing about IT rather than programming. My 20-year writing career has taken me to Hong Kong and London where I've edited and written for IT, business and electronics publications. In 2002 I co-founded Futurity Media with Stewart Baines where I continue to write about a range of topics such as unified communications, cloud computing and enterprise applications.