It looks like my intro to Private VLAN went over well, so I thought you might want to know more. I want to show anyone who’s still hesitant that things aren’t all that complicated once you get under the hood.
how it works
A Private VLAN always includes a primary VLAN (“Promiscuous,” as it contains “promiscuous ports”) and one or more secondary VLANs (two kinds: “Isolated” and “Community,” containing the “Host Ports”).
Each different VLAN will be on the same IP subnet (since only the primary VLAN will have a Level 3 interface or connect to the gateway by default).
to sum up...
Three different types of VLAN make up a Private VLAN infrastructure:
- Primary (Promiscuous): one machine configured as the primary VLAN can communicate with all other VLAN on the Private VLAN. This is typically used for routers and other shared services
- Isolated: completely separate at Layer 2 from other machines on the same VLAN (including broadcasts). The only exception is communication with primary VLAN machines
- Community: machines in the same community can communicate with each other and with primary VLAN machines. However, machines in one community cannot communicate with machines in another community or with isolated VLAN machines
In practice, secondary VLANs are linked to a primary VLAN, which has at least an exit router or firewall.
concrete scenarios with examples
"guest" zone scenario
For guest zones, we saw in the last article that isolating customers is essential (especially since more and more corporate employees are BYOD-friendly). To ensure this isolation, put the customers in an isolated VLAN and put the firewall in a primary VLAN.
This chart should help make it clear:
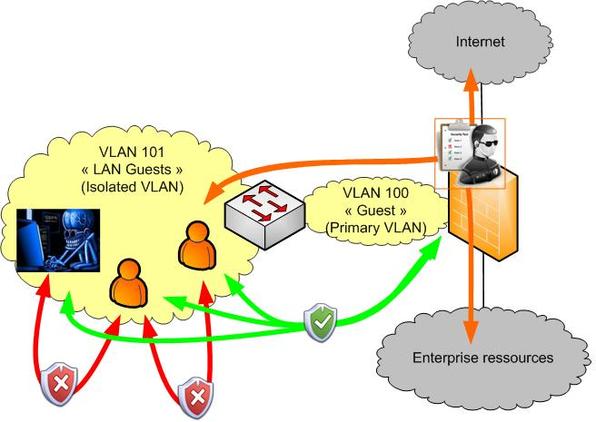
This will ensure proper isolation for each customer and enable monitored communication with the rest of the network by the firewall.
"DMZ" zone scenario
As for DMZ zones, the goal is to avoid having too many zones that each add extra interfaces (or subinterfaces) on the firewall.
One way to do so is to have proxy servers and SSL gateways in separate community VLANs, while still keeping your firewall in a primary VLAN.
Here’s what it looks like:
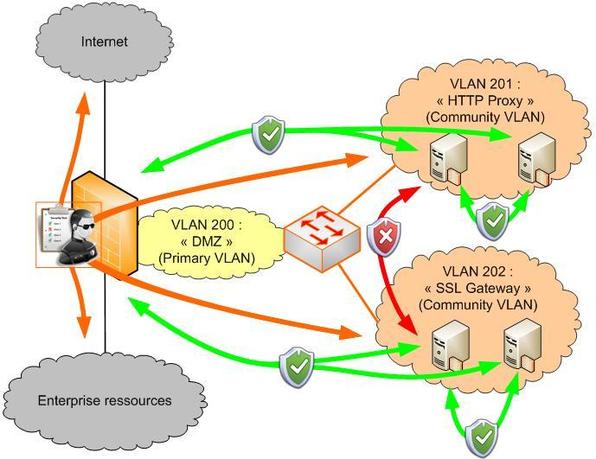
Here our servers can communicate directly within their community, but not with other communities. They share one common resource, namely the firewall, which monitors access to the rest of the network: LAN, WAN, and even other DMZ communities (if you authorize the firewall to enable and monitor communication between interfaces).
did that help clear things up about Private VLANs?
I hope these two short articles have explained some of what Private VLAN technology involves. Now you should be able to use this technology in your designs and add a little extra layer of security to your infrastructure.
Guillaume
for more information about Private VLANs => RFC 5517: http://tools.ietf.org/html/rfc5517
photo credit: © reji - Fotolia.com
Blog post originally published in French here.

I work at Econocom, where I’m currently a security architect for Cloud France solutions and its transversal services for Orange Business. I’m still new to the blog. My background is in networks and I’ve specialized in security since 2008. A huge technology buff with experience as a security integrator, I’m excited to contribute to the blog.
Edit from the Orange Business team: Guillaume left the Orange Group since he wrote his lasts posts.