Here goes my first article for our blog!
To start with, I’m no IT security expert. I know what you’re thinking, and I can already see a few grins out there because I say it all the time, but after a while, no one believes me anymore. No, I’m not an expert, nor am I an IT security technician! So don’t ask me how this or that protocol works, how to hack something, how to sniff out a network, or even what an IP address looks like (OK, I’m exaggerating a little, but not much), because I don’t know! My knowledge comes solely from experience working on projects I’ve led. In short, I’ll never talk to you about anything extremely technical.
The topic of the day is passwords. We say all the time that you have to change your password regularly. And that you need a strong password. But what does that mean? And why? How can someone crack a password?
cracking a password
There are three ways to crack a password: brute force, dictionary attacks and social engineering (in the IT sense, not in the political sense) .
Brute force is the easiest way to crack a password. It always yields a result if you have enough time on your hands (a lot of time in many cases). The technique is to simply try every possible password combination until you find the right one.
Dictionary attacks require a set, or “dictionary,” of possible passwords. In this method, you try all the words in the dictionary until you find the right combination. Obviously, if the right combination isn’t in the dictionary, you can’t crack the password.
However, these dictionaries are compiled from a set of common passwords. So statistically speaking, you have a high chance of cracking most users’ passwords.
Lastly, social engineering consists in sending a survey to users to obtain information about their life, family and other interests so as to find new password possibilities.
Some of you are probably rolling your eyes and want to tell me that websites only allow a certain number of password attempts. So it’s difficult to crack a password. But you also have to remember that passwords are generally stored on the computer used to enter them.
Fortunately, passwords are not easily found but they do leave a trace. You just have to try every possible password combination until you find the right trace.
change your password regularly
The more you change your password, the more you limit the risk of your password being used if it’s cracked and the more an attacker will have to redo the search process. This is the idea behind so-called strong logins, where you are assigned a “random” password. The more you reset the password, the less time attackers will have to crack it (for strong logins) and the lesser the chance they will have to use this password.
But always try to avoid one of the most common pitfalls: since people have to change their passwords so often, they tend to make them weaker to more easily remember them.
betting on strong passwords
Most people’s passwords only use the 26 letters of the alphabet. I won’t spend a lot of time on the different kinds of predictable passwords: kid’s names, pet’s names, “qwerty” or “password,” as well as short passwords because we’re usually pretty lazy when it comes to logins.
Today, the average password is only eight characters long. These passwords create 200 billion possible combinations. Since the average computer can run about 100 billion operations per second (with graphics capabilities, computers can sometimes reach more than two trillion operations per second), almost anyone’s computer can crack these passwords in about one second using brute force. That time is even shorter when using stronger calculation tools.
What happens if you use both upper and lowercase letters? The number of possible combinations will grow from 200 billion to 50 trillion. Now an attacker will need a lot more time to crack this password: a little over four minutes.
Basically, the more characters you use, the stronger your password becomes. That’s why you should always add more characters to your passwords: upper and lowercase letters, numbers, punctuation marks, and any other characters on your keyboard. When you use all the different types of characters available (approximately 90 characters in all), you expand the pool of possible combinations to four million billion. That means more than six hours of constant calculation to crack your password!
Six hours may seem like a lot but it’s still relatively fast. It’s even faster if you use more powerful calculation tools, like the power offered by cloud computing providers and botnets.
Since characters are limited, you have to use size to create even stronger passwords. With each extra character, you multiply the number of possible combinations by 100 which adds over 22 days to the time needed to crack the password. With this kind of password, attackers will really have to want to crack it. With each extra character, the process becomes exponentially more difficult.
The table below shows the total number of possible combinations for each password length. I also added the time needed for one of the biggest botnets ever created (Rustock, which was made up of about one million computers) to test every possible password combination (a calculation power that has yet to be equaled by any supercomputer or network, such as Folding@home).
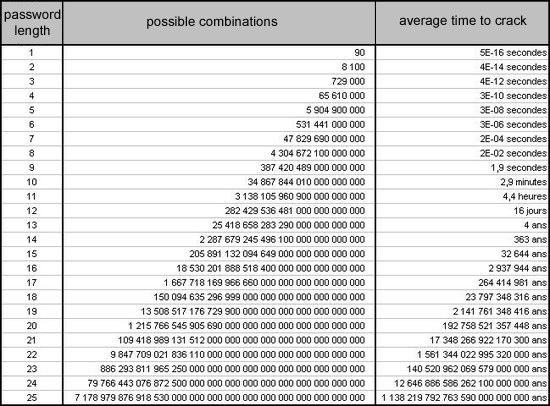
For comparison, remember that the Earth is only about 4.5 billion years old and the universe is about 13.7 billion years old . That’s less than the time needed to crack a password with 18 characters using current computing power.
It’s scary that most websites recommend passwords of at least eight or nine characters. It also goes to show the quality of advice on a lot of websites!
If your password has over 13 characters, you can assume it will be nearly uncrackable.
good passwords
To summarize, a good password uses every character type available on your keyboard, does not contain any word in any language or any names, and is at least 13 characters long. For now!
Yep, that only goes for now because computing power is growing exponentially. Average global computing power climbs by a factor of 10 about every four years. This means that in four years, we can assume that the biggest botnet available will have multiplied its power by the same factor. So the 13-character password that we recommend today will have to add another character to remain uncrackable.
Considering how long a strong password has to be, we’re really going to have to either improve our memories or come up with something a little more clever . We say password, but nothing says you have to use just one word. You can always make a passphrase based on a sentence you’ll remember.
For example, you’ll always remember your kid’s academic milestones with the phrase “Tom graduated in 2012.” Then you just use whatever method you like to blur the sentence a little: “T0mgr@duat3d1n2012.” That’s 19 characters, a nice variety of character types, and there’s no chance your password will be in any dictionary on Earth. So you can rest assured until you need another password.
hope you didn't fall asleep while reading my first article
Seb
This blog post was originally published in French here.
credit: Ben Chams - Fotolia.com

I’m in marketing and I’m a security product manager at Orange Business since 2009. My goal: popularize security and teach the average Joe about risks and solutions.