The phrase "Deep Web" refers to areas of the Internet not covered by traditional search engines. This may be due to content owners’ express desire or simply because search engines are unable to index these databases.
The extent of the Deep Web is still rather difficult to gauge, but experts agree that we’ve only seen the tip of the iceberg. That means there’s a lot of territory to explore.
One such tool for accessing this content is the onion router or “Tor” (along with Freenet, I2P and many more). Tor serves as a gateway to .onion websites. While it doesn’t cover the entire Deep Web, it does offer an interesting selection of uncharted material.
the Tor tool
Tor is a great tool which also enables users to surf the Web anonymously—an important feature in some situations. For both of these reasons, it definitely merits all the press it has attracted lately.
Personally, I cannot get over the fact that so many relays make navigation very slow. The screenshot below will give you an idea of what I mean.
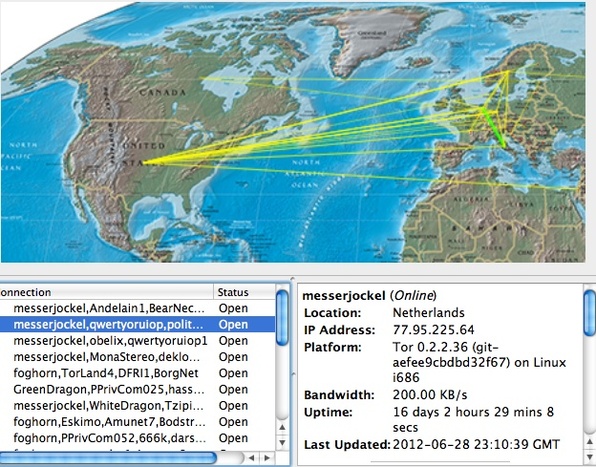
Nevertheless, in addition to its ability to access the Deep Web, Tor’s traffic encryption capabilities make it an interesting tool for people connecting via untrustworthy access points.
As for anonymous browsing, the tool makes it possible to change IP addresses with every connection. For more information on Tor and its features, you can read my colleague Jean-François’ blog entry.
diving into the shadowy depths
For new users like me, the Deep Web is full of excitement and possibility. And the idea of accessing sites with undistributed content is definitely cool. However, we must remember two important points:
- there is no global search engine, so you have to start with a list and work back and forth—which takes time, technique and a little luck
- even though the Deeeeeeep Web is a world of shadows and mystery, there is still a lot of junk and things that don’t work, so it takes time to find something worthwhile
To dive in, download Tor and use it to access this page. From here it’s possible to find a few interesting things, but I think the “needle in a haystack” expression is well suited to the situation.
A triumph for web history buffs: you can find a range of old documents and even museum pieces such as the official phreaker manual from 1987 on the Deep Web. It’s a good way to learn where modern techniques come from. In the case of phreaking, for example, many past approaches have been forgotten by security admins, so they can still cause a lot of damage.
Though these kinds of things are harmless, don’t forget that the Deep Web (at least the .onion version) is also a world crawling with drug dealers, pornography and shady activity of every sort. A little stroll through the woods can turn out to be a lot less innocent than it may seem at first glance. Be wary and use caution.
my final assessment
After several hours of tracking down links in the .onion zone, I concluded that the Deep Web is full of nutcases, pornography and vendors of more or less legal items.
The innocent first-timer arriving in this new neighborhood hoping to find some security pearls and learn some new tricks will end up a little disappointed. Apart from a few sites offering to work together to crack passwords, there isn’t anything very interesting.
To me, the .onion zone seems like a tool for creating a private, restricted workspace, not for accessing Deep Web areas without an introduction from someone from the community. In fact, the most interesting links I found came from a Google search…
Cedric
photo credit: © Victoria, fotolia.com

Membre actif de la communauté sécurité d'orange Business, je suis aujourd'hui en charge, au sein de l'équipe marketing « sécurité », de la bonne prise en compte de la sécurité dans nos offres traitant des communications sur IP, et cela du mode cloud à l'intégré classique. Un large périmètre pour rencontrer des problématiques complexes sur le plan technique comme sur le plan organisationnel. Bref, un océan de motivation pour toute personne qui marche au challenge et à l'envie d'apprendre.