However, willingness to embrace the potential productivity benefits of digital transformation also means accepting and mitigating new risks – and these risks are real. The U.S. Department of Homeland Security has warned that sustained cyberattacks against critical national infrastructure are ongoing, while the UK intelligence agency GCHQ (Government Communications Headquarters) has indicated that, "a number of industrial control system engineering and services organizations are likely to have been compromised."
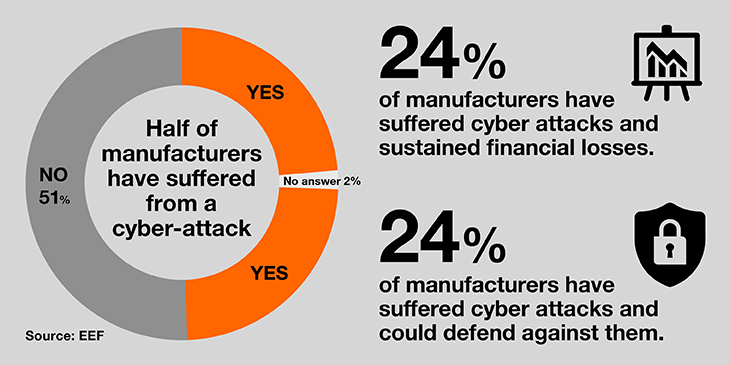
"More and more companies are at risk of attack and manufacturers urgently need to take steps to protect themselves against the burgeoning threat," said Stephen Phipson, Chief Executive of the UK Manufacturers' Organization (EEF). Failing to secure against such threats could cost money, jobs and threaten projects of national importance, the EEF say, observing that "nearly half" of all British manufacturers have already been attacked.
The Internet of Threat
One of the most famous attacks against connected industry remains the Stuxnet attack against Iran's uranium enrichment plant in 2007.
It isn't unique:
- In 2017, Ireland's Electricity Supply Board and an unnamed U.S.-based nuclear power plant were compromised
- In 2016, there were attacks targeting multiple European energy companies
- In 2015, hackers attacked a German steel mill causing major damage and used a backdoor Trojan called Duuzer to steal sensitive information from South Korean manufacturers
- In August 2012, Saudi Arabia's oil and gas sector fell victim to a coordinated attack, which infected 30,000 computer systems. It took two weeks to defeat
- A criminal attempt to cause storage facilities to explode was made against an unnamed Saudi Arabian petrochemical firm last year
More recently, a new type of malware called Trident was discovered, which undermines instrumented systems (SIS), enabling attackers to destroy or damage whatever processes those systems protect by feeding false data.
And we’re not just seeing attempts to damage infrastructure. Trend Micro and researchers at the university Politecnico di Milano have identified vulnerabilities in some existing industrial robots and controllers. Criminals could use such vulnerabilities to attack product quality. A component manufactured with a millimeter divergence from design could become a reputational crisis if it causes an accident, failure or injury.
Size makes no difference. Small firms that are connected to the global supply chain of larger enterprises may be attacked as criminals seek to use them as a gateway into systems belonging to their larger clients. A major smartphone manufacturer had to temporarily cease production of a critical component when its systems were infected by malware spread by a small third-party supplier.
As more connected systems are deployed, the opportunities for attacks against manufacturing will increase. Supply chain data (including payment information and confidential customer records) tempts criminals. A successful attack against just one element of a modern just-in-time supply chain could cause huge problems: who pays if food rots or heavy equipment goes to the wrong client? What happens when a disaffected employee abuses their position to penetrate secure systems?
Attackers aren’t just trying to cause damage or extort money. Many are focused on stealing trade secrets, plans and other valuable data. Reflecting the severity of that problem, Australia, the U.S. and UK reached a deal with China to stop such attacks in 2017, but this still leaves plenty of state and non-state actors in search of opportunities for mischief.
Take nothing for granted
Manufacturing is the second-most attacked industry, according to the IBM X-Force report 2017. EEF claims nearly 24 percent of its members have suffered loss as a result of cyberattack. With so many attacks taking place, why don’t we hear more about them?
A 2018 study by industrial supplier ERIKS found that of the 250 companies it surveyed, 79 percent would only share limited or no information with OEM partners if attacked. Manufacturers appear more concerned with protecting their reputation than collaborating for better security.
There is a skills gap when it comes to security in Industry 4.0. EEF claims almost half of manufacturers don’t feel they have access to the tools they need to assess their vulnerability to attack.
How can enterprises respond to this increasingly complex network of emerging threats and identify potential attack vectors before criminals exploit them?
Get real, be aware
Traditional protections – firewalls, malware protection, software patches, strictly enforced security policies around data and services access, as well as on-device security settings – will always have their place. Protection is also made far more robust when staff are equipped to recognize and react to any potential threat.
A security-first approach to the deployment of new connected systems is important. The prevalence of these attacks means a “build-it-and-forget-it” approach fails to recognize the true security environment, in which the fate of an enterprise, its partners or even national interest may be at stake.
With that in mind, enterprise purchasers must insist technology suppliers and connected equipment manufacturers commit to regular security and software patches and audits – anything less may leave systems vulnerable.
Threat intelligence, including monitoring of the dark web, also acts as an early warning system. It can uncover if cyber criminals are planning an attack, so the organization can pre-empt a breach and take immediate action to protect their digital corporate assets and physical infrastructure.
According to Cranfield University’s Professor Rajkumar Roy, real-time, sensor-based monitoring, software-defined and self-healing networks and mechanisms to isolate threats while leaving most systems functional, will form part of future manufacturing security protection.
As the pace of change accelerates and new technologies proliferate, the task of monitoring and understanding the emerging opportunities and evolving threats unleashed by this digital transformation is becoming a full-time task. Some enterprises respond to this with the creation of an executive Chief Security Officer (CSO) role, while others look to external firms to help provide situational awareness.
Read about how Orange Business can help secure your business from these and other emerging threats or download our infographic on the emerging threat landscape.

Jon Evans is a highly experienced technology journalist and editor. He has been writing for a living since 1994. These days you might read his daily regular Computerworld AppleHolic and opinion columns. Jon is also technology editor for men's interest magazine, Calibre Quarterly, and news editor for MacFormat magazine, which is the biggest UK Mac title. He's really interested in the impact of technology on the creative spark at the heart of the human experience. In 2010 he won an American Society of Business Publication Editors (Azbee) Award for his work at Computerworld.